CYBER PROTECTION

Can Cleaning Companies Beat the Hackers?

Elevate Your Cyber Defense with ISSA
In today’s increasingly digital environment your business’s security is paramount. Whether you realize it or not, cyber criminals are targeting small and mid-sized businesses at an alarming rate and you don’t want your firm to be the next victim.
In fact, Verizon reports that 43% of cyber attacks involve small businesses and the US National Cyber Security Alliance reports that 60% of small businesses that experience a cyber attack ultimately cease operations within six months. Additionally in 2023, the average cost of a network breach is $4.35M, a 15% increase over the past three years (IBM).
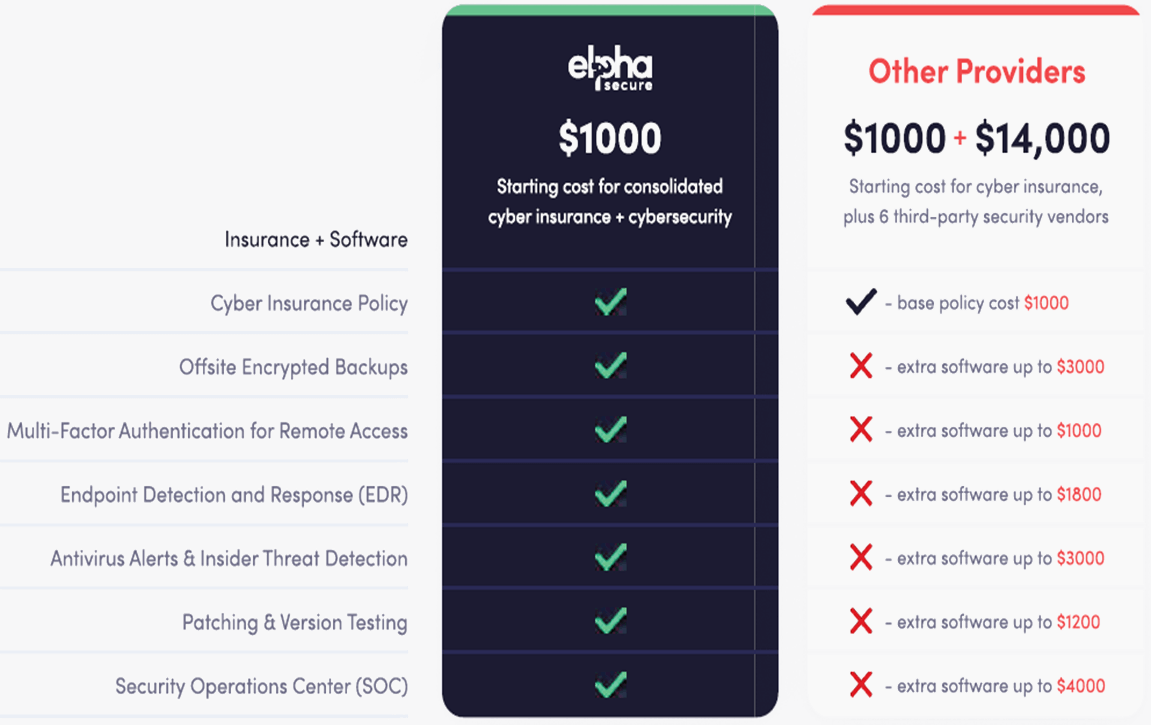
To help our members stay safe and minimize catastrophic business risks that result from cyber attacks, ISSA has partnered with CyberControls, powered by Elpha Secure and Bolton Street Programs to bring you a powerful blend of cyber insurance and cutting-edge security software—all at an affordable price point that’s exclusive to the ISSA-member community.
Explore the truth behind cyber insurance myths and real-world scenarios.

INTRODUCING THE ISSA CYBERSECURITY PROGRAM
ISSA’s new, meticulously vetted cyber assurance and insurance program is tailored to meet your unique business needs and offers unparalleled, proactive protection—assurance AND insurance—where you need it most.
Key Benefits
- Shield Against Cyber Threats
- Safeguard Company Assets and Finances
- Gain Peace of Mind with Proactive Protection

Leverage this unique solution to build a resilient business that’s ready to tackle cyber threats head-on.
Remember, cyber criminals are targeting businesses of all sizes, and the consequences of an attack can be devastating. Secure your business’s digital future with ISSA and our exclusive program.
Common Questions to Purchasing Cyber Insurance
Cybercriminals don’t discriminate. In fact, smaller companies are more susceptible due to their lack of security controls. It is a numbers game. Small businesses are not targeted but they are subject to “spray and pray” campaigns where bad actors attack thousands of organizations at once, through sophisticated scanning technology, looking for common vulnerabilities and exposures (CVEs) that they can exploit. In layman’s terms, it’s equivalent to the cat burglar driving down the road looking for open windows to crawl into. However, they are doing it on a much larger scale, from a remote location, with little chance of ever getting caught. The most important thing a small business can do to not be a victim is to ensure the windows and doors are locked and install an alarm system. Furthermore, there is an entire ecosystem of bad actors selling compromised credentials (passwords) on the dark web, enabling the cat burglars to show up with keys to your door. While security controls can prevent most of these attacks, even the most sophisticated organizations will still have cracks in their security posture. That is where insurance is paramount.
It is important to address the misconception that small businesses are not at risk of cyber attacks. In fact, Verizon reports that 43% of cyber attacks involve small businesses and the US National Cyber Security Alliance reports that 60% of small businesses that experience a cyber attack ultimately cease operations within six months. Moreover, ransomware threat actors are increasingly targeting small businesses to evade law enforcement attention. This trend is particularly concerning as there has been a rise in cyber attacks on sole proprietors.Approximately 31% of cyber attacks target sole proprietorships, which not only has a significant impact on their business but also on their personal lives.
Lastly, it is becoming the norm for organizations to require vendors and their supply chain to have cyber insurance in place. Over the next few years, all commercial contracts are likely to include cyber insurance as a requirement.
This is a misconception. Cyber exposure consists of a multitude of different things such as employee negligence, disgruntled employees, use of the internet (malware on websites), devil routers (unsecured free wifi), accidental physical hardware damage, invoice manipulation, wire fraud, and many more.
As long as you use email and the internet, you are vulnerable.
More than 75% of cyber-attacks are initiated by an individual’s act of opening a malicious email. In the past two years, Business Email Compromise incidents have surpassed the frequency of ransomware attacks. Additionally, cyber exposure is not exclusive to computer-related incidents; it can also address vulnerabilities related to paper records. Loss or theft of sensitive paper documents, such as client information or financial records, can lead to identity theft, regulatory fines, and reputational damage. Cyber insurance can provide coverage for the costs associated with investigating and managing such incidents, including notifying affected parties, legal expenses, and potential data recovery.
This is another misconception. You can outsource a service or a task, but you still retain all the cyber risk. In the event of a data breach, your company is responsible for the legal, regulatory, and compliance burden of stolen customer data. Insurance covers all the costs associated with remediation, notification, and regulatory compliance.
Elpha Secure is specifically designed to combat this exact concern for small businesses. We provide a set of tools for free within the policy premium to help you begin your cyber security journey. We provide Multi-Factor Authentication for Remote Access, Backups, and Endpoint Detection and Response (a real-time threat detector). These tools are all backed by our internal 24/7 Security Operations Center.
We are partnered with eRiskHUB and CYGNVS to provide free pre- and post-breach educational services to all of our Insureds. We also train your employees on the Elpha product if needed. Furthermore, we ensure that our insureds receive regular security bulletins, which keep them updated on the latest news and developments in the field of cyber threat intelligence. Additionally, we generate educational and informative blog articles to empower our insured and help them stay well-informed on relevant topics.
Our MFA, along with all of our tools, is a very simple implementation process. We only require it for remote access into your network.
Also, our customer success team can help walk you through how MFA works as well. All that is required is a cell phone to receive an SMS text message or authenticator code to confirm your identity. We do not require it on email or anywhere else, but we can assist your team with enabling MFA on your email accounts as an option.
We provide a suite of proprietary cyber security tools in addition to your traditional cyber insurance policy. No one else on the market is doing this – our competitors have vendor relationships with contracts in place to satisfy minimum costs. We own our tools and provide them for free. More importantly, we differentiate ourselves by delving below the surface when it comes to cybersecurity. Many cyber insurance companies focus solely on the “attack surface” the visible vulnerabilities that can be identified through external scanning. However, this narrow approach provides only a glimpse of an lnsured’s security posture representing only the easily detectable 10% that anyone with basic scanning tools can uncover. This in essence is tantamount to security theater which only provides Insureds with a false sense of security. We understand it is vital to go below the surface in order to truly protect our Insureds and proactively prevent claims. By gaining deep insights into the remaining 90%, we are able to uncover vulnerabilities that can elude traditional scanning methods. Elpha Secure’s unique combination of cyber insurance, end point software, and 24/7 Security Operations Center (“soc”) provides a holistic approach to an organization’s security. We leverage traditional risk transfer, technology, and human intelligence to help organizations prevent, prepare, and respond to a cyber incident.
This is a loaded question. Generally, your IT team is in place to build the network infrastructure and maintain day-to-day operations. We do not solve for that, but provide additional support to the Insured in their security. However, we have had clients remove/cancel their existing tools (ex. MFA) during their onboarding process with Elpha Secure and move forward with our products.
It’s important to note traditional cyber carriers typically conduct outside-in scans, which are aimed at identifying potential vulnerabilities from outside the organization’s network. In contrast, Elpha Secure conducts both outside-in and inside-out scans to identify vulnerabilities that could be exploited by cybercriminals, whether they are trying to gain unauthorized access from outside the network or have already infiltrated the internal network. If any alerts come back with high severity, our Security Operations team will proactively engage with the Insured and assist them with remediating the alert before it matures into a Cyber Incident.
While Elpha has very competitive premium rates, some of the biggest savings are due to not having to purchase additional security software to qualify for insurance. This is the case with most of the carriers. Controls such as Backups, MFA, Security patching, etc. are typically required via a pre-bind subjectivity. These can be costly and in many cases, multiples of the premium being charged. With Elpha, you get it all included in your premium.
If you already have MFA, backups, or EDR, we don’t necessarily need to be the software you choose. We can either be a redundant layer alongside your pre-existing software or you can replace it with our software if you are looking for a more budget-conscious approach.
You can also choose to use all of your own software and purchase a standard cyber insurance policy from us as well.
For support contact [email protected]
© 1998- ISSA. All rights reserved | Privacy Policy